The Vulnerability
The attacks targets port 7547 that runs a service named TR-069 –a protocol that’s used for remotely managing CPE’s from an ACS server (CWMP – CPE WAN Management Protocol). The CPE in this case is modem and ACS servers push commands to CPE – For example upgrading firmware.
In routers such as Eir D1000 there’s also another use of this port 7547 that runs a TR-064 server. As per Zyxel - “TR064 describes a specific implementation to be used for DSL CPE LAN-side configuration. The management application can be a software program or an installation CD from the CPE vendor”. This service is supposedly not accessible from WAN but that wasn’t the case in Eir D1000 modems.
The Attack
Attackers took advantage of this vulnerability and went about targeting them rigorously. A contrived attack packet looks like below,
The bash file when executed downloads an ELF executable from 185.35.139.92 and executes it.
Details of the files are below,
- ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
- ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
- ELF 32-bit LSB executable, ARM, version 1, statically linked, stripped
All of these files had the same functionality. For the purpose of
analysis I took “ELF MIPS LSB executable”. With the limited set of tools
(that I was able to setup) for performing dynamic analysis I ran the
malware directly on an emulated environment to understand the behaviour.
When
running the malware it initially copied itself into the memory and
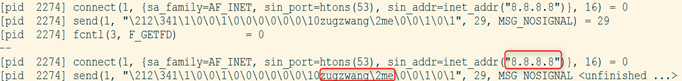
deleted itself and also uses Google’s DNS server (8.8.8.8) to resolve
the C2 domain (zugzwang.me).
Further analysis on the logs gathered it was observed that the malware used “iptables” to drop incoming connections on multiple ports. This is to ensure that there are no further infections on the device from other malwares.
The malware then proceeds to infect other devices by scanning the internet for open port 7547.
And the exploit that’s sent is also visible in the memory that was dumped. So the cycle of reinfecting other routers continue by using this exploit.






No comments:
Post a Comment